After parts 1 and 2 we can safely say the machine is infected.This next part will go through the building of the MandiantIOC using Ioc Editor in order to hopefully identify other infected hosts.
One issue I am keeping an eye on is trying to identify indicators that would hopefully be present in numerous samples. Malware writers are incorporating new ways to subvert AV identification techniques (And have been know to brag online that the malware is not detected).
Driver Inspection
I’m going to start with the driver (imjvxcsr.sys) associated with the misspelled service: Micorsoft Windows Service.Looking at the drivers name it looks randomly generated but after infecting the same host a few times the driver name is consistent on the host.
The directory where the driver is located always seems to be C:\Documents and Settings\User\Local Settings\Temp as seen in the SSDT hooks tab in Audit Viewer and Redline
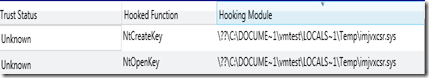
Using Redline to review Drivers and Devices we can see that we have a device also associated with the driver
By selecting the Driver and reviewing the driver information we can review any strings associated with the driver.
Upon reviewing the Strings we can see an number of possible IOCs
- \systemsroot\temp\%x
- \Device\631D2408D44C4f47AC647AB96987D4D5
- \DosDevices\631D2408D44C4f47AC647AB96987D4D5
- c:\project\demetra\loader~1\drivers\ssdt\driver~1\objfre_win7_x86\i386\SdtRestore.pdb
Using the OpenIOC Framework we can start with the following
- Driver StringList is c:\project\demetra\loader~1\drivers\ssdt\driver~1\objfre_win7_x86\i386\SdtRestore.pdb
- Driver StringList is \Device\631D2408D44C4f47AC647AB96987D4D5
- Driver StringList is \DosDevices\631D2408D44C4f47AC647AB96987D4D5
Hook Inspection
If we then review the Hooks section using Redline or Audit Viewer we can use it to further enhance our indicator.Using the evidence above we can use the Hooking Module, Hooked Module and Hook Description.
Using the OpenIOC Framework we can use the following to enhance our IOC
- Hook HookDescription is SystemCall
- Hook Hooking Module contains \Local~1\Temp\
- Hook Hooked Module is ntoskrnl.exe
Process Inspection
Using the default indicator from Redline and Audit Viewer we can build an IOC for the svchost.exe with unexpected arguments (this can be expanded on if your environment has additional valid svchost arguments) .- Process name is svchost.exe
- Process arguments is not C:\WINDOWS\System32\svchost.exe -k netsvcs
- Process arguments is not C:\WINDOWS\system32\svchost -k rpcss
- Process arguments is not C:\WINDOWS\System32\svchost.exe -k LocalService
- Process arguments is not C:\WINDOWS\System32\svchost.exe -k NetworkService
- Process arguments is not C:\WINDOWS\system32\svchost -k DcomLaunch
- Process arguments is not C:\WINDOWS\system32\svchost.exe -k imgsvc
There are other string values that look to be passwords, email addresses and DNS hostnames.
By reviewing the String List below we can also make the assumption that Ramnit has integrated some of the components seen in Zeus, these references can be found in the leaked source code which can be found online.
- Process Handle contains \Start Menu\Programs\Startup\
- Process Handle contains CTF.Compart.MutexDefaultS-1-5-21
- Process Handle contains CTF.Layouts.MutexDefaultS-1-5-21
- Process Handle contains CTF.TMD.MutexDefaultS-1-5-21
- Process Handle contains CTF.TimListCache.FMPDefaultS-1-5-21
- Process Handle contains CTF.Asm.MutexDefaultS-1-5-21
- Process Handle contains CTF.LBES.MutexDefaultS-1-5-21
- Process String contains LOCALS~1\Temp\~TM4.tmp
- Process String is Hide Browser v1.1
- Process String is 220 220 RMNetwork FTP
- Process String is Ftp Grabber v1.0
- Process String is Virus Module v1.0 (exe, dll only)
- Process String is VNC Module v1.0 (Zeus Model)
- Process String is Byob Ernie Gild Lotto 2002-2006
- Process String is Reich.exe
- Process String is \Start Menu\Programs\Startup\
- Process String is <%IDBOT%><%REMOTE={*}%><#{*} {*}#>ECHOADDSUBSETDATECONTENT POST
- Process Handle Name is !IETld!Mutex
- Process StringList is \\.\631D2408D44C4f47AC647AB96987D4D5
By reviewing the NETWORK ACTIVITY Section for Install.exe (PID 3424) we can assume this is our spamming engine. By reviewing the Process Strings can can confirm this functionality.
Further review shows reference to Delphi and in particular what looks to be a backup location for the source code. A number of stings also mention a few Email clients\providers(Outlook,The Bat, POPPeeper).
Using the OpenIOC one possible IOC could be the following:
- Process StringList is X:\old_backup\Delphi\Mailer4\cl\Sources\clMailMessage.pas
- Process StringList is X:\old_backup\Delphi\Mailer4\cl\Sources\clSocket.pas
- Process StringList isX:\old_backup\Delphi\Mailer4\cl\Sources\clCertificate.pas
- Process StringList is X:\old_backup\Delphi\Mailer4\cl\Sources\clSspiTls.pas
- Process StringList is X:\old_backup\Delphi\Mailer4\cl\Sources\clTlsSocket.pas
- Process StringList isX:\old_backup\Delphi\Mailer4\cl\Sources\clSocks.pas
- Process StringList is X:\old_backup\Delphi\Mailer4\cl\Sources\clTcpClient.pas
- Process StringList is TModule_POPPeeper
- Process StringList is TModule_Eudora
- Process StringList is TModule_Gmail
- Process StringList is TModule_IncrediMail
- Process StringList is TModule_GroupMailFree
- Process StringList is TModule_VypressAuvis
- Process StringList is TModule_The_Bat
- Process StringList is TModule_Outlook0
- Process StringList is TOutlookIdentItem
Published IOC
All we need to do now is put it together and introduce the logic to get the hits.A complete IOC that has been tested is below, the IOC has been tested against multiple audit files and did not produce and false positives.OR:
- DriverItem/StringList/string is ' c:\project\demetra\loader~1\drivers\ssdt\driver~1\objfre_win7_x86\i386\SdtRestore.pdb'
- DriverItem/StringList/string is ' \Device\631D2408D44C4f47AC647AB96987D4D5'
- DriverItem/StringList/string is ' 631D2408D44C4f47AC647AB96987D4D5'
- ProcessItem/HandleList/Handle/Name is ' !IETld!Mutex'
- ProcessItem/StringList/string is ' \\.\631D2408D44C4f47AC647AB96987D4D5'
- ProcessItem/StringList/string contains ' <%IDBOT%><%REMOTE={*}%><#{*} {*}#>ECHOADDSUBSETDATECONTENT POST'
- AND:
- HookItem/HookDescription is ' SystemCall'
- HookItem/HookedModule is ' ntoskrnl.exe'
- HookItem/HookingModule contains ' \LOCALS~1\Temp\'
- AND:
- ProcessItem/StringList/string contains ' Micorsoft Windows Service'
- ProcessItem/StringList/string contains ' TANGrabber'
- ProcessItem/name is ' services.exe'
- AND:
- ProcessItem/arguments isnot ' C:\WINDOWS\System32\svchost.exe -k netsvcs'
- ProcessItem/arguments isnot ' C:\WINDOWS\system32\svchost -k rpcss'
- ProcessItem/arguments isnot ' C:\WINDOWS\System32\svchost.exe -k LocalService'
- ProcessItem/arguments isnot ' C:\WINDOWS\System32\svchost.exe -k NetworkService'
- ProcessItem/arguments isnot ' C:\WINDOWS\system32\svchost -k DcomLaunch'
- ProcessItem/arguments isnot ' C:\WINDOWS\system32\svchost.exe -k imgsvc'
- ProcessItem/name is ' svchost.exe'
- AND:
- ProcessItem/name is ' svchost.exe'
- OR:
- ProcessItem/HandleList/Handle/Name contains ' CTF.Compart.MutexDefaultS-1-5-21'
- ProcessItem/HandleList/Handle/Name contains ' CTF.Layouts.MutexDefaultS-1-5-21'
- ProcessItem/HandleList/Handle/Name contains ' CTF.TMD.MutexDefaultS-1-5-21'
- ProcessItem/HandleList/Handle/Name contains ' CTF.TimListCache.FMPDefaultS-1-5-21'
- ProcessItem/HandleList/Handle/Name contains ' CTF.Asm.MutexDefaultS-1-5-21'
- ProcessItem/HandleList/Handle/Name contains ' CTF.LBES.MutexDefaultS-1-5-21'
- ProcessItem/HandleList/Handle/Name contains ' \Start Menu\Programs\Startup\'
- ProcessItem/StringList/string contains ' LOCALS~1\Temp\~TM4.tmp'
- ProcessItem/StringList/string is ' Hide Browser v1.1'
- ProcessItem/StringList/string is ' 220 220 RMNetwork FTP'
- ProcessItem/StringList/string is ' Ftp Grabber v1.0'
- ProcessItem/StringList/string is ' Virus Module v1.0 (exe, dll only)'
- ProcessItem/StringList/string is ' VNC Module v1.0 (Zeus Model)'
- ProcessItem/StringList/string is ' Byob Ernie Gild Lotto 2002-2006'
- ProcessItem/StringList/string is ' Reich.exe'
- AND:
- ProcessItem/StringList/string is ' X:\old_backup\Delphi\Mailer4\cl\Sources\clMailMessage.pas'
- ProcessItem/StringList/string is ' X:\old_backup\Delphi\Mailer4\cl\Sources\clSocket.pas'
- ProcessItem/StringList/string is ' X:\old_backup\Delphi\Mailer4\cl\Sources\clCertificate.pas'
- ProcessItem/StringList/string is ' X:\old_backup\Delphi\Mailer4\cl\Sources\clSspiTls.pas'
- ProcessItem/StringList/string is ' X:\old_backup\Delphi\Mailer4\cl\Sources\clTlsSocket.pas'
- ProcessItem/StringList/string is ' X:\old_backup\Delphi\Mailer4\cl\Sources\clSocks.pas'
- ProcessItem/StringList/string is ' X:\old_backup\Delphi\Mailer4\cl\Sources\clTcpClient.pas'
- ProcessItem/StringList/string is ' TModule_POPPeeper'
- ProcessItem/StringList/string is ' TModule_Eudora'
- ProcessItem/StringList/string is ' TModule_Gmail'
- ProcessItem/StringList/string is ' TModule_IncrediMail'
- ProcessItem/StringList/string is ' TModule_GroupMailFree'
- ProcessItem/StringList/string is ' TModule_VypressAuvis'
- ProcessItem/StringList/string is ' TModule_The_Bat'
- ProcessItem/StringList/string is ' TModule_Outlook0'
- ProcessItem/StringList/string is ' TOutlookIdentItem'
Happy Hunting, Please leave feedback if the IOC produces false positives and needs amending or improving.




5 comments:
I’m going to start with the driver (imjvxcsr.sys) associated with the misspelled service: Micorsoft Windows Service.
By this, do you mean driver with a misspelled Windows service Display Name?
Harlan thanks for reading the post.
You are correct, when you review the image path Registry entry (HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ Services \ Micorsoft Windows Service)\Image Path) for the service it corresponds to the rootkit driver.
Sorry for the confusion.
Again, I'm confused...you say "misspelled service", but what you showed (i.e., the misspelled "Micorsoft") doesn't appear to be what would be present in the ImagePath value...rather, it appears that it would be what appears in the DisplayName value.
Now, if this is what appears in the ImagePath value, I would consider that to be a very significant IOC...
Harlan again you are correct regarding the misspelled service.
The Display name shows the misspelled Service and the image path points to the rootkit driver which is loaded.
I also agree they are pretty good IOC's although the malware can easily be recompiled to create a service with a different Display Name and also different Image Path value. Hopefully the other indicators would still be triggered.
Hello I'm trying to build up myself a IOC for Zeus V2 and I'm getting stuck trying to formalize the Ring 3 hooks established from explorer exe to USER32.dll, CRYPT32.dll. How can I do that?
Also I would like to know if there is any kind of cheatsheet for IOC indicators.
Thanks for all
Post a Comment