Memory Analysis
Please note the memory sample reviewed in this next section does not correlate with the logs reviewed above (I.E PIDs are different, and one other artifact occurred during the memory dump. All will be revealed)
After the VM was snapshot and paused analysis could be conducted on the vmem file.
A number of tools were used to conduct the analysis including the following:
- Mandiant’s Redline (and also AuditViewer with Memoryze)
- Volatility
The reason a number of tools were used was because each tool has advantages and disadvantages.
Process List and Process Tree
The output below was generated from Volatility using the pslist command. As can been seen below Sample1.exe is the ParentPID of two svchost.exe processes (The snapshot was taken before Sample1.exe terminated see Ramnit Zeus and Bat part 1).
During one of the infections an additional process was started by one of the svchost.exe (PID 2000) the process was called install.exe (PID 3424). We will analyse the file later.
Offset(V) Name PID PPID Thds Hnds Time
---------- -------------------- ------ ------ ------ ------ -------------------
0x823c8830 System 4 0 67 510 1970-01-01 00:00:00
0x82193da0 smss.exe 556 4 3 19 2012-01-11 22:13:40
0x81fff978 csrss.exe 624 556 12 732 2012-01-11 22:13:43
0x81f67978 winlogon.exe 648 556 21 519 2012-01-11 22:13:43
0x81ef7880 services.exe 692 648 20 298 2012-01-11 22:13:43
0x81f91418 lsass.exe 704 648 27 424 2012-01-11 22:13:43
0x82209198 vmacthlp.exe 860 692 5 40 2012-01-11 22:13:44
0x81e654f0 svchost.exe 872 692 25 223 2012-01-11 22:13:44
0x81ea7360 svchost.exe 956 692 15 284 2012-01-11 22:13:45
0x81f42c10 svchost.exe 1068 692 93 1600 2012-01-11 22:13:45
0x81e9c528 svchost.exe 1200 692 10 93 2012-01-11 22:13:46
0x822adbf0 svchost.exe 1300 692 18 177 2012-01-11 22:13:46
0x822bc840 spoolsv.exe 1428 692 18 133 2012-01-11 22:13:46
0x81e1e6a0 svchost.exe 1532 692 9 116 2012-01-11 22:13:55
0x81e28da0 EngineServer.ex 1604 692 8 53 2012-01-11 22:13:55
0x81e755e8 FrameworkServic 1628 692 14 238 2012-01-11 22:13:55
0x820353e8 VsTskMgr.exe 1692 692 28 273 2012-01-11 22:13:58
0x82194a58 mfevtps.exe 1716 692 10 157 2012-01-11 22:13:59
0x822537a8 naPrdMgr.exe 1724 872 9 98 2012-01-11 22:13:59
0x81ee8760 VMwareService.e 1928 692 7 157 2012-01-11 22:13:59
0x81e4dda0 Mcshield.exe 2012 692 17 131 2012-01-11 22:14:00
0x81de7968 mfeann.exe 204 2012 13 127 2012-01-11 22:14:05
0x81eff6a0 explorer.exe 708 492 23 616 2012-01-11 22:14:08
0x81fb0a20 alg.exe 524 692 10 117 2012-01-11 22:14:32
0x8223bda0 VMwareTray.exe 1048 708 5 50 2012-01-11 22:14:33
0x81ecb588 wscntfy.exe 416 1068 5 51 2012-01-11 22:14:33
0x821ec918 VMwareUser.exe 1464 708 10 212 2012-01-11 22:14:34
0x8225f6a8 UdaterUI.exe 1612 708 10 121 2012-01-11 22:14:35
0x81f22a20 shstat.exe 900 708 0 ------ 2012-01-11 22:14:35
0x81e81550 AdobeARM.exe 2092 708 12 197 2012-01-11 22:14:38
0x81d1fda0 ctfmon.exe 2216 708 5 89 2012-01-11 22:14:39
0x81f047c8 McTray.exe 2296 1612 5 46 2012-01-11 22:14:39
0x81f8d7b0 mcconsol.exe 3796 900 9 176 2012-01-11 22:15:12
0x81cf3a20 cmd.exe 2108 708 5 53 2012-01-11 22:15:47
0x81f1c5c8 CaptureBAT.exe 2992 2108 0 ------ 2012-01-11 22:16:13
0x81fc8ab0 CaptureBAT.exe 3788 2108 10 56 2012-01-11 22:16:57
0x8213f458 Sample1.exe 4000 708 0 ------ 2012-01-11 22:17:04
0x821e1bf0 svchost.exe 2640 4000 13 125 2012-01-11 22:17:05
0x82070200 svchost.exe 2000 4000 10 119 2012-01-11 22:17:05
0x820b9ad0 install.exe 3424 2000 12 159 2012-01-11 22:17:42
0x82049b60 iexplore.exe 2200 708 0 ------ 2012-01-13 19:36:33
0x81a629b8 iexplore.exe 516 708 26 367 2012-01-13 19:37:49
0x81a535a0 iexplore.exe 2480 516 27 550 2012-01-13 19:37:51
Upon analysing the memory dump using Redline the following processes are flagged straight away and highlighted red.
svchost.exe PID 2000
svchost.exe PID 2640
Redline reports that the reason the processes were flagged was due to both processes having unexpected arguments in fact the processes don't have any.
“C:\WINDOWS\system32\svchost.exe”
We get a different visual representation of the memory dump using Mandiant’s Memoryze and Audit Viewer.
The reason for all the additional flags is due to the fact that Audit Viewer has identified the injected memory sections.
Redline also displays the Injected Memory Sections and upon initial analysis it can be seen that they nearly all start at the the same Region address:0x20010000
Network Activity
Offset(V) Local Address Remote Address Pid
---------- ------------------------- ------------------------- ------
0x820c0008 192.168.0.18:1806 173.194.41.95:80 2480
0x81e307a8 192.168.0.18:1810 173.194.67.104:80 2480
0x81ab0008 192.168.0.18:1807 209.85.147.94:80 2480
0x82066a58 192.168.0.18:1802 204.212.40.2:25 3424
0x81f65a50 192.168.0.18:1052 209.85.147.105:80 2000
0x81a994f0 192.168.0.18:1809 209.85.147.94:80 2480
0x81a994f0 192.168.0.18:1805 209.85.147.94:80 2480
0x81f29720 192.168.0.18:1033 209.85.147.105:80 2000
0x82055008 192.168.0.18:1500 209.85.229.99:80 2000
0x8206c370 192.168.0.18:1803 74.125.43.27:25 3424
0x81a9db28 192.168.0.18:1799 202.136.110.213:25 3424
0x81a9db28 192.168.0.18:1715 202.136.110.213:25 3424
Straight away the interesting connections that stand out are the connections to port 25 (SMTP) this will be expanded on later. The IP Addresses are located in Australia, and The United States
Services
Using Volatility (svcscan) we can review the Services that were running at the time the snapshot was taken, upon first analysis nothing really seems to be amiss apart from the misspelled: Micorsoft Windows Service
Offset(P) #Ptr #Hnd Start Size Service key Name
0x01f26f38 3 0 0xb2746000 333952 'Srv' 'Srv' '\\FileSystem\\Srv'
0x01fe0190 3 0 0xf8b72000 15488 'mssmbios' 'mssmbios' '\\Driver\\mssmbios'
0x01fe0838 3 0 0xf80f5000 384768 'Update' 'Update' '\\Driver\\Update'
0x01fe3950 2 0 0xb2102000 68512 'mfeapfk' 'mfeapfk' '\\Driver\\mfeapfk'
0x01fffa08 5 0 0xf8ab6000 11008 'vmscsi' 'vmscsi' '\\Driver\\vmscsi'
0x02042a18 5 0 0xb1e81000 264832 'HTTP' 'HTTP' '\\Driver\\HTTP'
0x0204bf38 5 0 0xf88ba000 56576 'mfetdik' 'mfetdik' '\\Driver\\mfetdik'
0x0204cb10 4 0 0xb2cc0000 113152 'vmhgfs' 'vmhgfs' '\\FileSystem\\vmhgfs'
0x0204f300 3 0 0xf883a000 41472 'RasPppoe' 'RasPppoe' '\\Driver\\RasPppoe'
0x02060df0 19 0 0xf8376000 333376 'mfehidk' 'mfehidk' '\\Driver\\mfehidk'
0x02061860 5 0 0xf83c8000 105344 'Mup' 'Mup' '\\FileSystem\\Mup'
0x02061ce8 17 0 0xf83e2000 182656 'NDIS' 'NDIS' '\\Driver\\NDIS'
0x02064bb8 3 0 0xf882a000 51328 'Rasl2tp' 'Rasl2tp' '\\Driver\\Rasl2tp'
0x02071168 6 0 0xf853b000 125056 'Ftdisk' 'Ftdisk' '\\Driver\\Ftdisk'
0x0207b240 3 0 0xf8a82000 21760 'TDTCP' 'TDTCP' '\\Driver\\TDTCP'
0x0207d178 2 0 0xb21db000 11648 'CaptureFileMonitor' 'CaptureFileMonitor' '\\FileSystem\\CaptureFileMonitor'
0x02091790 3 0 0xf88ca000 34688 'NetBIOS' 'NetBIOS' '\\FileSystem\\NetBIOS'
0x02092f38 5 0 0xb2cfe000 162816 'NetBT' 'NetBT' '\\Driver\\NetBT'
0x02095838 5 0 0xf8153000 196224 'rdpdr' 'rdpdr' '\\Driver\\rdpdr'
0x02096030 4 0 0xf8263000 12160 'mouhid' 'mouhid' '\\Driver\\mouhid'
0x02098030 7 0 0xf8bb0000 7936 'Fs_Rec' 'Fs_Rec' '\\FileSystem\\Fs_Rec'
0x0209cf38 6 0 0xf8972000 23040 'Mouclass' 'Mouclass' '\\Driver\\Mouclass'
0x020ab1b0 6 0 0xf84fd000 96512 'atapi' 'atapi' '\\Driver\\atapi'
0x020ab2a8 5 0 0xf86ba000 52352 'VolSnap' 'VolSnap' '\\Driver\\VolSnap'
0x020ab3a0 4 0 0xf8922000 19712 'PartMgr' 'PartMgr' '\\Driver\\PartMgr'
0x020b2030 4 0 0xf87fa000 40704 'es1371' 'es1371' '\\Driver\\es1371'
0x020bcf38 3 0 0xf89c2000 19072 'Msfs' 'Msfs' '\\FileSystem\\Msfs'
0x020bd030 3 0 0xf8b52000 13952 'CmBatt' 'CmBatt' '\\Driver\\CmBatt'
0x020bd560 3 0 0xf89ca000 30848 'Npfs' 'Npfs' '\\FileSystem\\Npfs'
0x020c2548 3 0 0xf86ea000 42368 'agp440' 'agp440' '\\Driver\\agp440'
0x020e8be0 3 0 0xf8c26000 7296 'CaptureRegistryMonitor' 'CaptureRegistryMonitor' '\\Driver\\CaptureRegistryMonitor'
0x020fd788 4 0 0xb2c25000 455296 'MRxSmb' 'MRxSmb' '\\FileSystem\\MRxSmb'
0x02101790 3 0 0xb2cdc000 138496 'AFD' 'AFD' '\\Driver\\AFD'
0x02101be0 7 0 0xb2d74000 361600 'Tcpip' 'Tcpip' '\\Driver\\Tcpip'
0x02103678 6 0 0xf88aa000 59520 'usbhub' 'usbhub' '\\Driver\\usbhub'
0x02106bd8 3 0 0xf8bb6000 4224 'RDPCDD' 'RDPCDD' '\\Driver\\RDPCDD'
0x02126928 3 0 0xb27e8000 180608 'MRxDAV' 'MRxDAV' '\\FileSystem\\MRxDAV'
0x02128970 4 0 0xb1c2d000 143744 'Fastfat' 'Fastfat' '\\FileSystem\\Fastfat'
0x02130730 3 0 0xf89a2000 16512 'Raspti' 'Raspti' '\\Driver\\Raspti'
0x02134360 2 0 0xb20ed000 84352 'mfeavfk' 'mfeavfk' '\\Driver\\mfeavfk'
0x02134880 3 0 0xb25a6000 60800 'sysaudio' 'sysaudio' '\\Driver\\sysaudio'
0x02161160 4 0 0xf8b9e000 5504 'IntelIde' 'IntelIde' '\\Driver\\IntelIde'
0x02164cc0 3 0 0xf8d3a000 2944 'Null' 'Null' '\\Driver\\Null'
0x0216f030 7 0 0xf8cd2000 3072 'audstub' 'audstub' '\\Driver\\audstub'
0x02170110 5 0 0xf89d2000 32128 'usbccgp' 'usbccgp' '\\Driver\\usbccgp'
0x0218f6e0 3 0 0xf885a000 35072 'Gpc' 'Gpc' '\\Driver\\Gpc'
0x0218fbb8 5 0 0xf8183000 69120 'PSched' 'PSched' '\\Driver\\PSched'
0x021905f0 13 0 0x00000000 0 '\\Driver\\Win32k' 'Win32k' '\\Driver\\Win32k'
0x021a1030 4 0 0xf896a000 24576 'Kbdclass' 'Kbdclass' '\\Driver\\Kbdclass'
0x021ada30 6 0 0xf8515000 153344 'dmio' 'dmio' '\\Driver\\dmio'
0x021adc48 3 0 0xf8ba0000 5888 'dmload' 'dmload' '\\Driver\\dmload'
0x021f09f8 5 0 0xf887a000 40704 'TermDD' 'TermDD' '\\Driver\\TermDD'
0x021fdec8 3 0 0xf8325000 12032 'WS2IFSL' 'WS2IFSL' '\\Driver\\WS2IFSL'
0x02209030 3 0 0xf881a000 36352 'intelppm' 'intelppm' '\\Driver\\intelppm'
0x0220bda0 3 0 0xf87da000 48256 'vmci' 'vmci' '\\Driver\\vmci'
0x02222460 3 0 0xf8bb4000 4224 'mnmdd' 'mnmdd' '\\Driver\\mnmdd'
0x02230270 5 0 0xb2411000 83072 'wdmaud' 'wdmaud' '\\Driver\\wdmaud'
0x02232f38 3 0 0xb2c95000 175744 'Rdbss' 'Rdbss' '\\FileSystem\\Rdbss'
0x02236408 3 0 0xf8335000 8832 'RasAcd' 'RasAcd' '\\Driver\\RasAcd'
0x02236ca8 3 0 0xf89ba000 20992 'VgaSave' 'VgaSave' '\\Driver\\VgaSave'
0x0223bcc0 3 0 0xf8bb2000 4224 'Beep' 'Beep' '\\Driver\\Beep'
0x022f11e8 3 0 0xf8952000 32768 'Micorsoft Windows Service' 'Micorsoft Windows Service' '\\Driver\\Micorsoft Windows Service'
0x02349500 3 0 0xb17f2000 172416 'kmixer' 'kmixer' '\\Driver\\kmixer'
0x02389bb8 9 0 0xf8bac000 4352 'swenum' 'swenum' '\\Driver\\swenum'
0x0238ef38 6 0 0xf826b000 10368 'hidusb' 'hidusb' '\\Driver\\hidusb'
0x0239b7f0 6 0 0xf899a000 17792 'Ptilink' 'Ptilink' '\\Driver\\Ptilink'
0x0239c5d8 3 0 0xf88ea000 36864 'vmdebug' 'vmdebug' '\\Driver\\vmdebug'
0x023a04b8 4 0 0xf87ca000 57600 'redbook' 'redbook' '\\Driver\\redbook'
0x023a6418 3 0 0xf8b96000 10624 'gameenum' 'gameenum' '\\Driver\\gameenum'
0x023e9030 3 0 0xf873a000 63744 'Cdfs' 'Cdfs' '\\FileSystem\\Cdfs'
0x023ea5d0 3 0 0xf8c1e000 6272 'CaptureProcessMonitor' 'CaptureProcessMonitor' '\\Driver\\CaptureProcessMonitor'
0x023fcf38 2 0 0xb21bb000 36288 'mfebopk' 'mfebopk' '\\Driver\\mfebopk'
0x02405740 3 0 0xb2dcd000 75264 'IPSec' 'IPSec' '\\Driver\\IPSec'
0x024178d0 5 0 0xf878a000 52480 'i8042prt' 'i8042prt' '\\Driver\\i8042prt'
0x02437da0 3 0 0xb1eea000 139520 'RDPWD' 'RDPWD' '\\Driver\\RDPWD'
0x02439030 3 0 0xf8be2000 6784 'ParVdm' 'ParVdm' '\\Driver\\ParVdm'
0x02439430 3 0 0xb2a59000 14592 'Ndisuio' 'Ndisuio' '\\Driver\\Ndisuio'
0x02439da0 3 0 0xf8be4000 7680 'VMMEMCTL' 'VMMEMCTL' '\\Driver\\VMMEMCTL'
0x02450f38 3 0 0xf88fa000 44544 'Fips' 'Fips' '\\Driver\\Fips'
0x02458a50 3 0 0xb2d4e000 152832 'IpNat' 'IpNat' '\\Driver\\IpNat'
0x0245d030 3 0 0xf87aa000 42112 'Imapi' 'Imapi' '\\Driver\\Imapi'
0x0245d610 3 0 0xf87ba000 62976 'Cdrom' 'Cdrom' '\\Driver\\Cdrom'
0x024682a0 4 0 0xf8234000 91520 'NdisWan' 'NdisWan' '\\Driver\\NdisWan'
0x02468d78 6 0 0xf8b56000 10112 'NdisTapi' 'NdisTapi' '\\Driver\\NdisTapi'
0x02472640 4 0 0xf8309000 80128 'Parport' 'Parport' '\\Driver\\Parport'
0x024ad8a8 3 0 0xf898a000 29696 'vmxnet' 'vmxnet' '\\Driver\\vmxnet'
0x024b3b70 16 0 0xf84c5000 129792 'FltMgr' 'FltMgr' '\\FileSystem\\FltMgr'
0x024c00b0 7 0 0xf86aa000 42368 'MountMgr' 'MountMgr' '\\Driver\\MountMgr'
0x024edca8 3 0 0xf890a000 34560 'Wanarp' 'Wanarp' '\\Driver\\Wanarp'
0x024ef838 3 0 0xf884a000 48384 'PptpMiniport' 'PptpMiniport' '\\Driver\\PptpMiniport'
0x024efb30 3 0 0xf89aa000 20480 'Flpydisk' 'Flpydisk' '\\Driver\\Flpydisk'
0x024f9150 3 0 0xf8ba8000 4736 'vmmouse' 'vmmouse' '\\Driver\\vmmouse'
0x0250d290 4 0 0xf897a000 27392 'Fdc' 'Fdc' '\\Driver\\Fdc'
0x0250e278 4 0 0xf8982000 20608 'usbuhci' 'usbuhci' '\\Driver\\usbuhci'
0x0250f200 4 0 0xf8b4a000 15744 'serenum' 'serenum' '\\Driver\\serenum'
0x0250f378 3 0 0xf87ea000 57216 'vmx_svga' 'vmx_svga' '\\Driver\\vmx_svga'
0x0250f9f8 4 0 0xf879a000 64512 'Serial' 'Serial' '\\Driver\\Serial'
0x02517c78 3 0 0xf888a000 40576 'NDProxy' 'NDProxy' '\\Driver\\NDProxy'
0x02519778 4 0 0xf840f000 574976 'Ntfs' 'Ntfs' '\\FileSystem\\Ntfs'
0x02519988 3 0 0xf849c000 92288 'KSecDD' 'KSecDD' '\\Driver\\KSecDD'
0x02519b98 7 0 0xf84b3000 73472 'sr' 'sr' '\\FileSystem\\sr'
0x0251ccc8 4 0 0xf86ca000 36352 'Disk' 'Disk' '\\Driver\\Disk'
0x0253e218 4 0 0xf8aae000 10240 'Compbatt' 'Compbatt' '\\Driver\\Compbatt'
0x025ab560 5 0 0x00000000 0 'RAW' '\\FileSystem\\RAW'
0x025acf38 81 0 0xf855a000 68224 'PCI' 'PCI' '\\Driver\\PCI'
0x025af2d8 4 0 0x00000000 0 '\\Driver\\ACPI_HAL' 'ACPI_HAL' '\\Driver\\ACPI_HAL'
0x025c5308 4 0 0xf869a000 37248 'isapnp' 'isapnp' '\\Driver\\isapnp'
0x025e2980 64 0 0xf856b000 187776 'ACPI' 'ACPI' '\\Driver\\ACPI'
0x025e6ce8 4 0 0x00000000 0 '\\Driver\\WMIxWDM' 'WMIxWDM' '\\Driver\\WMIxWDM'
0x025eb290 65 0 0x00000000 0 '\\Driver\\PnpManager' 'PnpManager' '\\Driver\\PnpManager'
Using the driverirp Volatility command we can output a drivers IRP (Major Function) table, here we can see that we have a driver (imjvxcsr.sys) associated with the misspelled Micorsoft Windows Service
0xf8952000 'Micorsoft Windows Service' IRP_MJ_CREATE 0xf89541b8 imjvxcsr.sys - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_CREATE_NAMED_PIPE 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_CLOSE 0xf89541b8 imjvxcsr.sys - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_READ 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_WRITE 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_QUERY_INFORMATION 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_SET_INFORMATION 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_QUERY_EA 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_SET_EA 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_FLUSH_BUFFERS 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_QUERY_VOLUME_INFORMATION 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_SET_VOLUME_INFORMATION 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_DIRECTORY_CONTROL 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_FILE_SYSTEM_CONTROL 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_DEVICE_CONTROL 0xf89541d8 imjvxcsr.sys - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_INTERNAL_DEVICE_CONTROL 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_SHUTDOWN 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_LOCK_CONTROL 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_CLEANUP 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_CREATE_MAILSLOT 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_QUERY_SECURITY 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_SET_SECURITY 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_POWER 0xf89541b8 imjvxcsr.sys - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_SYSTEM_CONTROL 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_DEVICE_CHANGE 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_QUERY_QUOTA 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_SET_QUOTA 0x804f355a ntoskrnl.exe - -
0xf8952000 'Micorsoft Windows Service' IRP_MJ_PNP 0x804f355a ntoskrnl.exe - -
Hooks
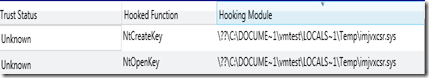
If we review the Hooks tab in Audit Viewer or the Hooks section in Redline and in particular the System Service Descriptor Table Hooks we see our driver (imjvxcsr.sys) identified in the previous section
This can also be verified using the ssdt or the threads –F HookedSSDT Volatility commands.
ssdt command
Entry 0x0029: 0xf89546ac (NtCreateKey) owned by imjvxcsr.sys
Entry 0x0077: 0xf8954562 (NtOpenKey) owned by imjvxcsr.sys
threads –F HookedSSDT command
ETHREAD: 0x81f1cbc8 Pid: 692 Tid: 3980
Tags: HookedSSDT
Created: 2012-01-11 22:18:34
Exited: -
Owning Process: 0x81ef7880 'services.exe'
Attached Process: 0x81ef7880 'services.exe'
State: Waiting:WrQueue
BasePriority: 0x9
Priority: 0x9
TEB: 0x7ffd9000
StartAddress: 0x7c8106f9
ServiceTable: 0x80553020
[0] 0x80501b9c
[0x29] NtCreateKey 0xf89546ac imjvxcsr.sys
[0x77] NtOpenKey 0xf8954562 imjvxcsr.sys
[1] -
[2] -
[3] -
Win32Thread: 0x00000000
CrossThreadFlags:
Eip: 0x7c90e514
eax=0x77e76c7d ebx=0xffffffff ecx=0x00090640 edx=0x0072fb78 esi=0x000ac2e8 edi=0x00000000
eip=0x7c90e514 esp=0x006efeac ebp=0x006efed8 err=0x00000000
cs=0x1b ss=0x23 ds=0x23 es=0x23 gs=0x00 efl=0x00000246
dr0=0x00000000 dr1=0x00000000 dr2=0x00000000 dr3=0x00000000 dr6=0x00000000 dr7=0x00000000
Part 3 Building an IOC to follow.



1 comment:
Hi! Nice post. I was wondering how you loaded a vmem into redline ?
Post a Comment